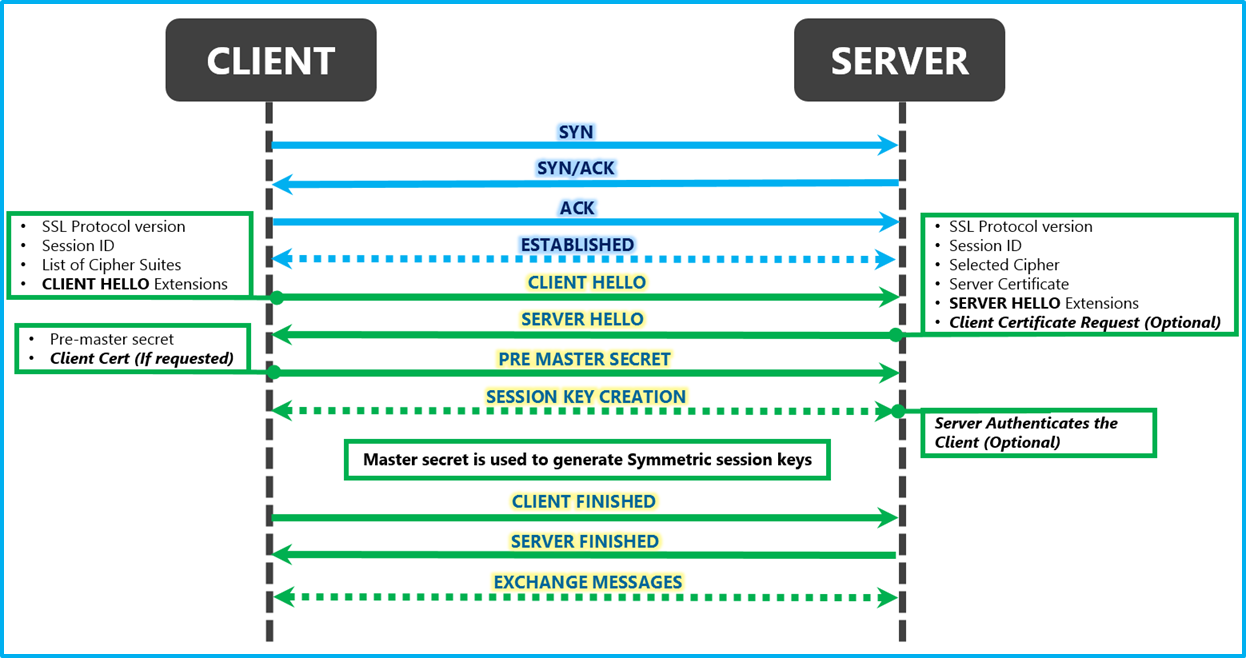
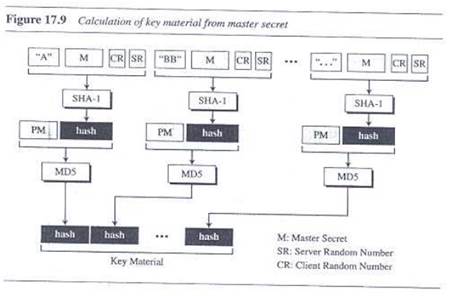
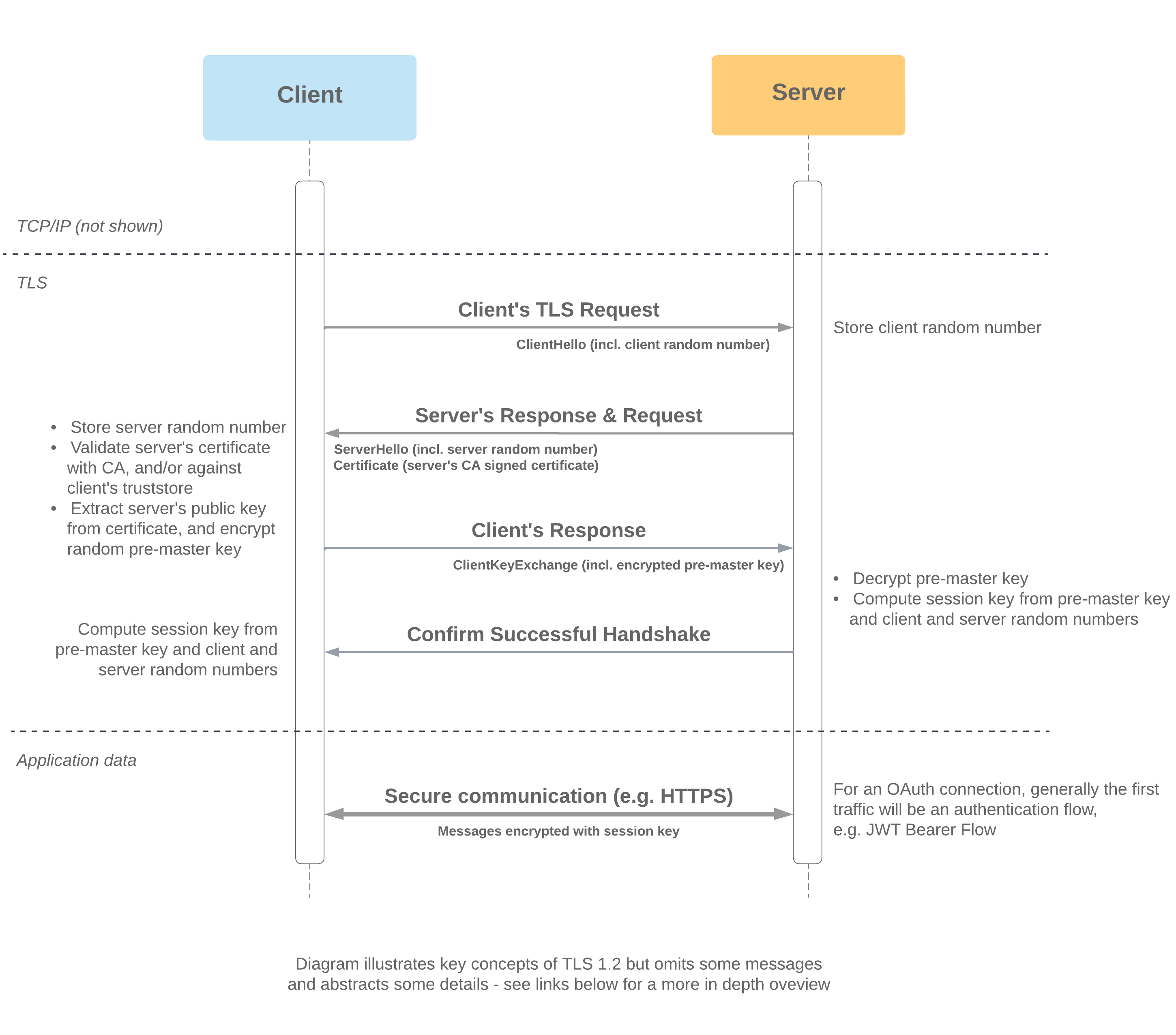
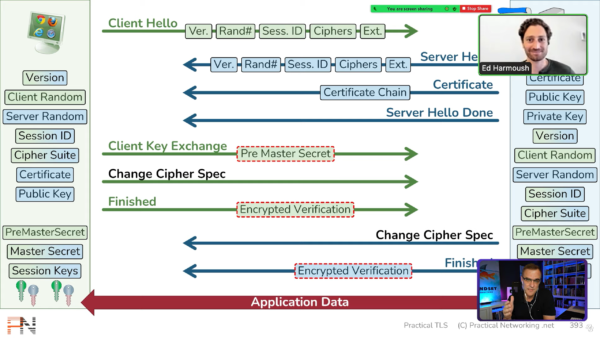
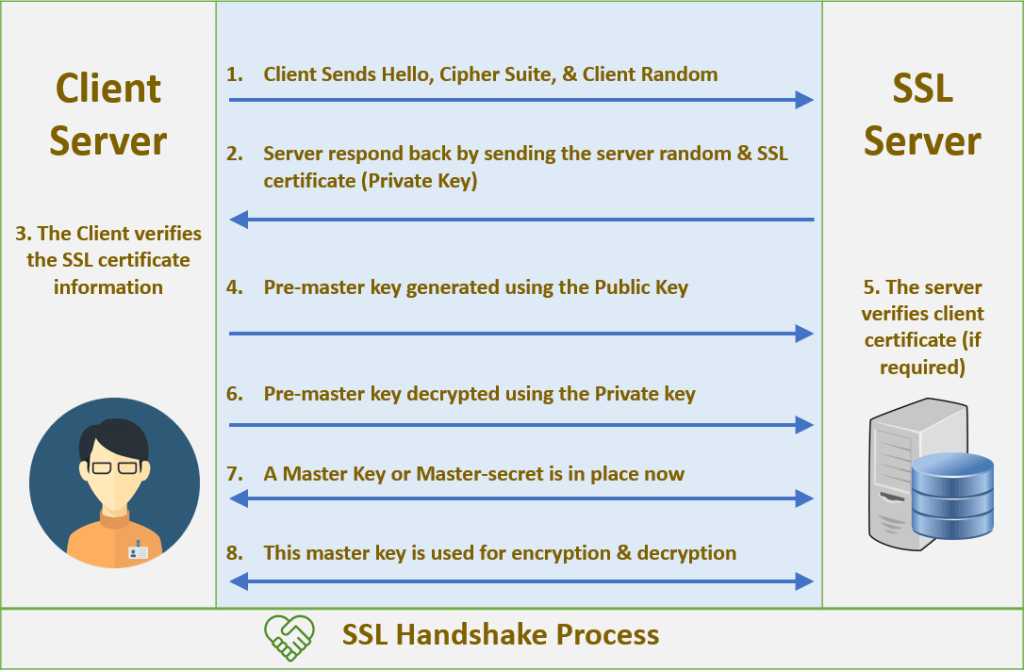
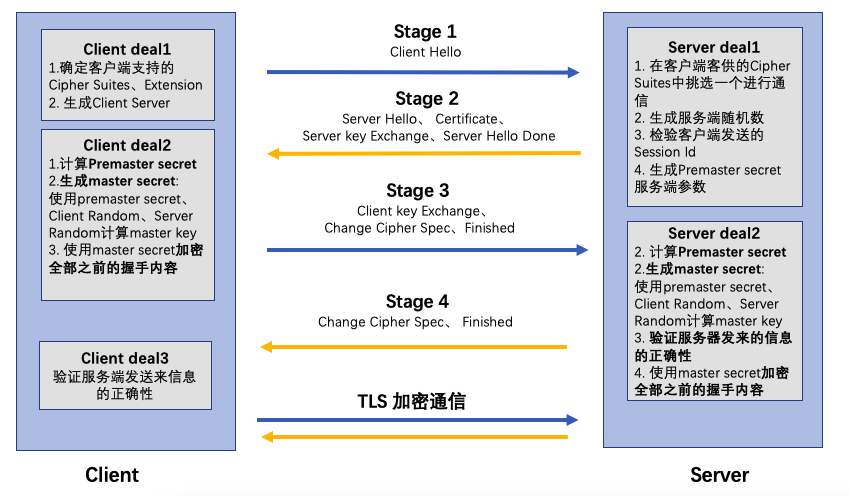
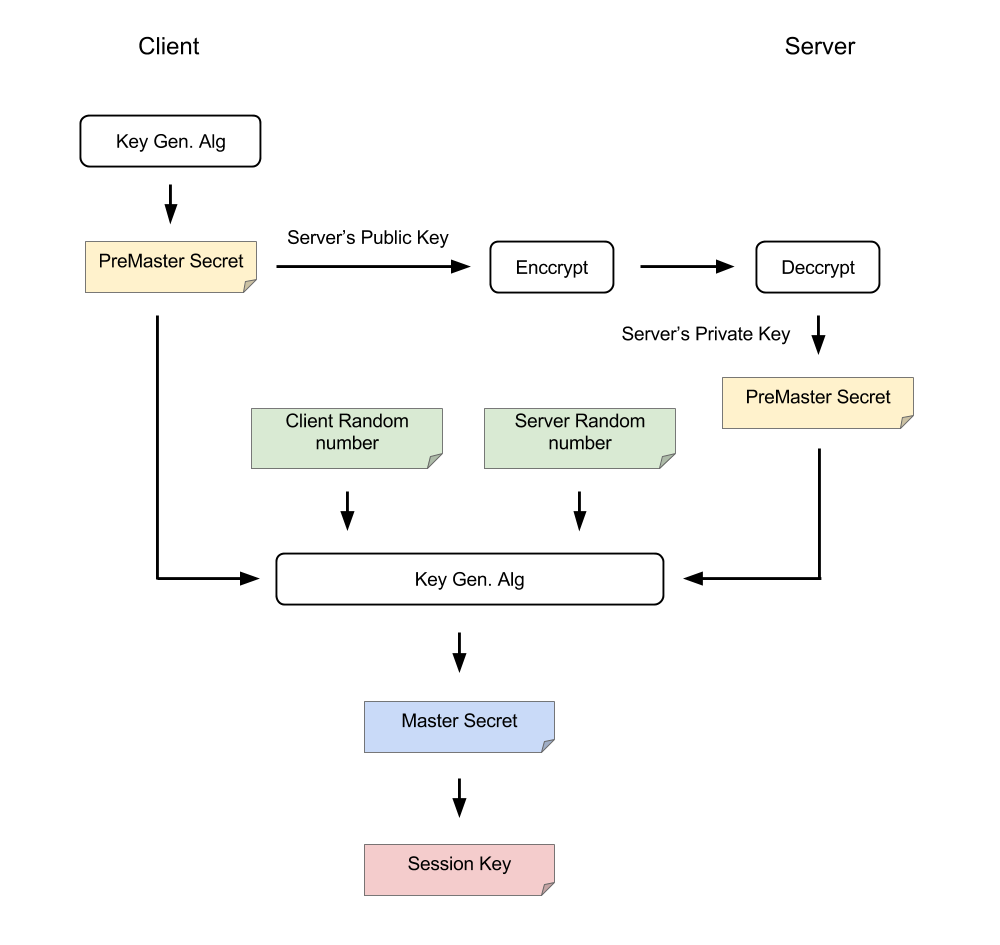
tls - Differences between the terms "pre-master secret", "master secret", "private key", and "shared secret"? - Cryptography Stack Exchange

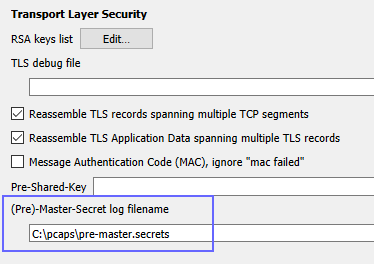
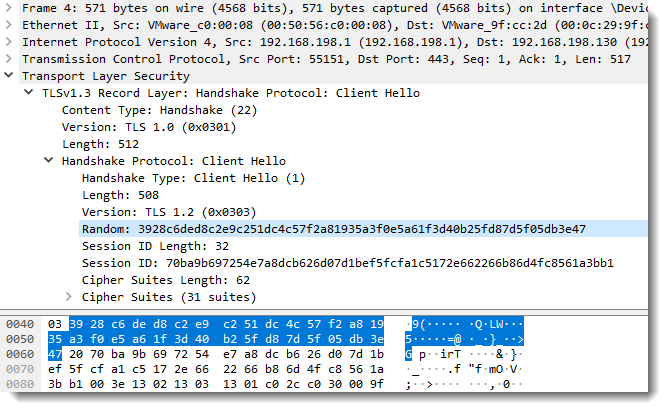
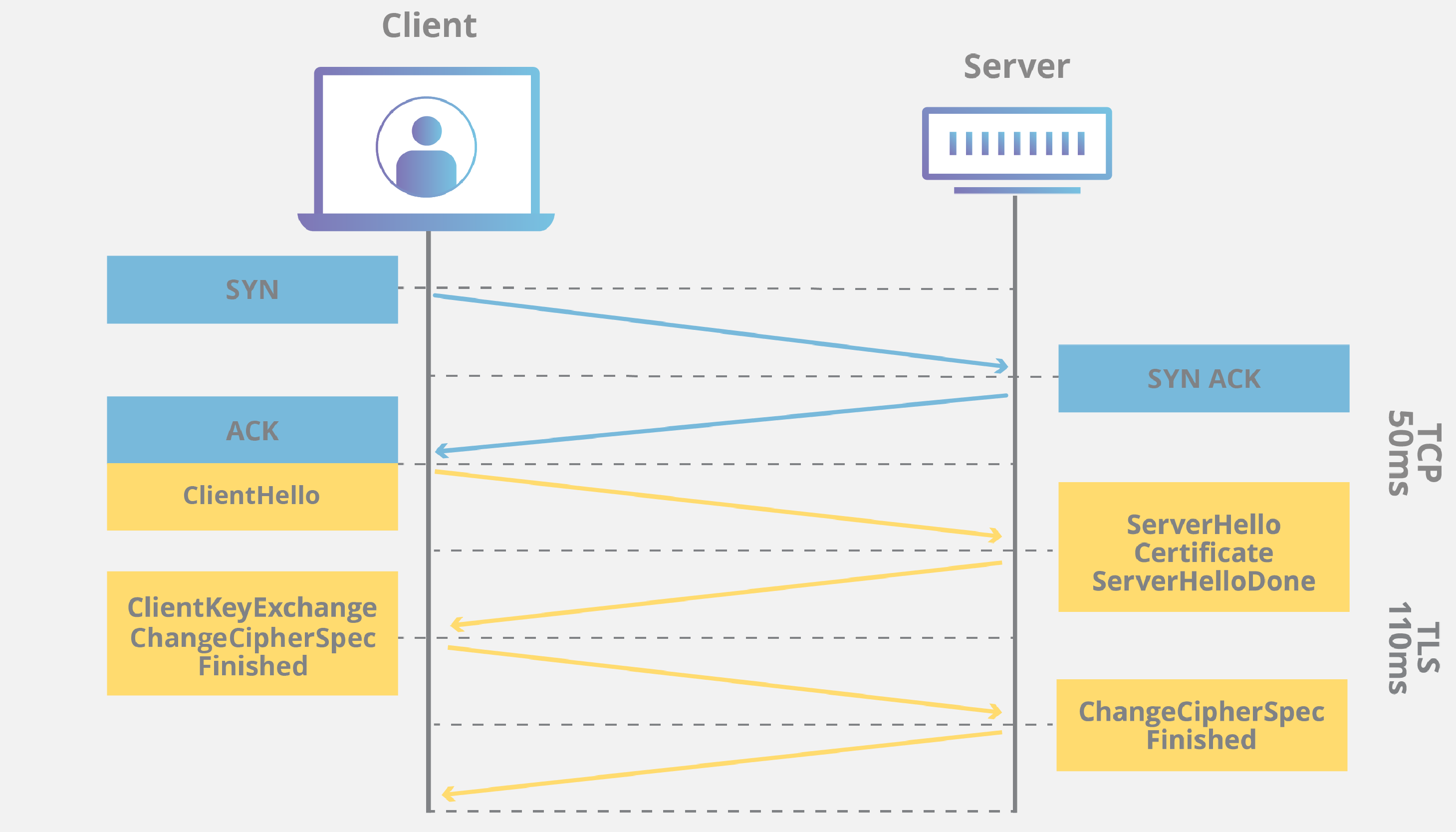
Decrypting TLS Streams With Wireshark: Part 2 - Malware Analysis - Malware Analysis, News and Indicators
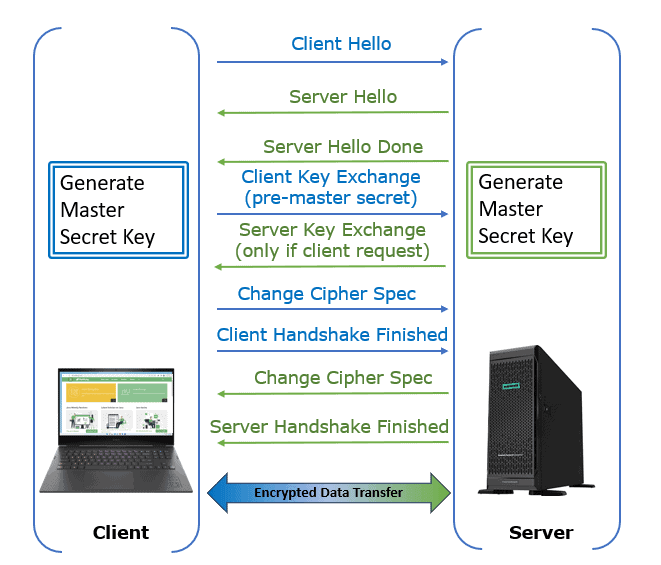
Pre-master Secret vs. Master Secret vs. Private Key vs. Shared Secret | Baeldung on Computer Science